As technology continues to evolve, businesses are looking for solutions that can ensure data privacy and security. Confidential Computing and Blockchain technology provide these solutions, but they are often misunderstood. Let’s take a look at what confidential computing is, how it works, and why it matters.
What is Confidential Computing?
Confidential computing is the practice of processing sensitive information in a secure environment. It ensures that data remains encrypted while being processed in the cloud or on-premises systems. This eliminates the risk of data breaches or other malicious activities. By using confidential computing, businesses can securely process sensitive data without having to worry about unauthorized access or manipulation during the processing.
How Confidential Computing works?
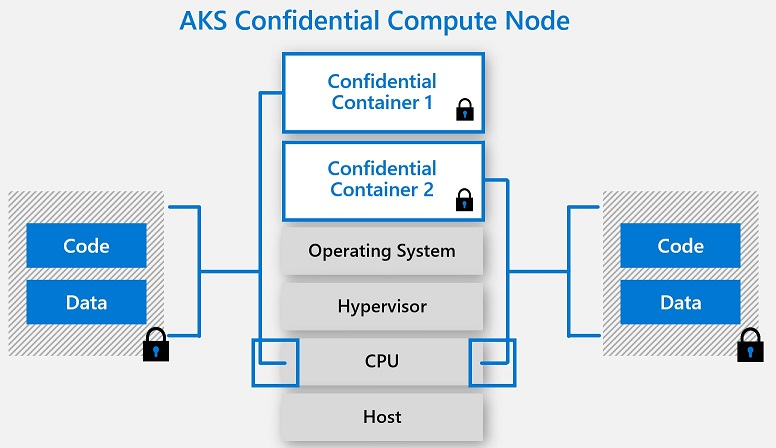
Confidential computing provides an additional layer of security by using Trusted Execution Environments (TEEs) to protect sensitive data from being accessed by third-party malicious actors as the data never leaves its encrypted form, even when it’s being processed by applications running on cloud-based networks. This makes Confidential computing a great option for businesses that need to store and process large amounts of confidential information, such as financial institutions, and medical companies, without compromising their security. The most common TEEs used are Intel SGX, Windows Virtual Secure Mode (VSM), or ARM TrustZone but that is subject to another post.
What About Blockchain?
Blockchain technology is another method of securing sensitive information. It utilizes a distributed ledger system that allows for secure transactions between two parties without intermediaries or third-party involvement. This ensures that all transactions are transparent and secure as each transaction is cryptographically signed and stored on multiple computers around the world so there’s no single point of failure or potential breach point for hackers to exploit. In addition, blockchain technology also provides enhanced privacy as all transactions are anonymous and unchangeable once committed to the ledger.
Put it all together!
Confidential Computing and blockchain technology provides powerful solutions for protecting sensitive information while processing it in a secure environment. By utilizing these technologies, businesses can ensure their data remains safe from malicious actors while still providing a high level of performance and reliability for their customers' needs. For CIOs, CTOs, and other tech managers who need to ensure their data remains secure, these technologies are invaluable tools in safeguarding their customers' information while remaining competitive in today's digital landscape.
BBChain | BlockchainLab
At BBChain, we understand the importance of privacy and data security for businesses. We use blockchain technology and confidential computing at BlockchainLab to provide a secure platform for our customers that ensures the security of their sensitive information. Our solutions are designed to protect against malicious actors accessing or manipulating customer data while it is being processed in the cloud or on-premise.